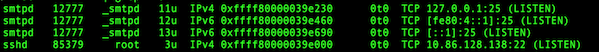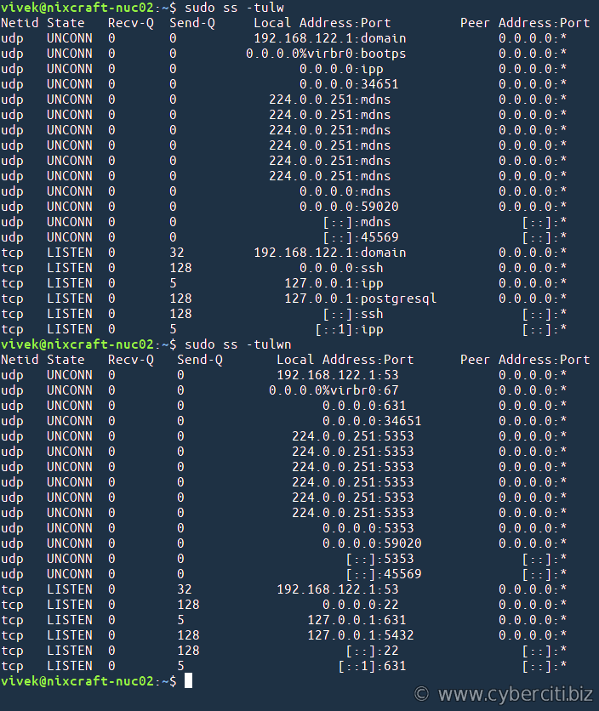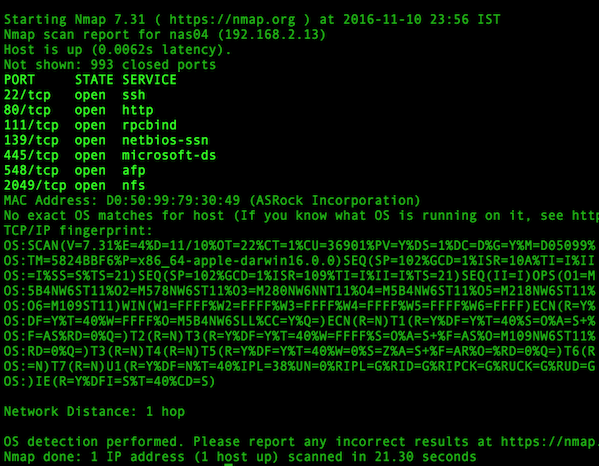
In 2023 I flushed the old Swann video system (NVR) and replaced it with a Mini PC (AMD Ryzen 7 - 4 core) running Ubuntu 22.04 and Zoneminder with MariaDb, apache2, php, and perl. The swann required proprietary software (Windows .exe) and I wanted to be able to look at any camera or the Zoneminder console or from any computer in the house (all Linux). I also wanted to add more cameras. To accomplish this I needed to add POE switches to my home network. Due to existing cat5 and location of new cams, I put a 5 port 1Gb POE switch in Betty's Office, and an 8 port 1Gb POE switch in my office. After looking at the amount of traffic, I decided to move the camera traffic to a dedicated Video Network, accessable from the main home net. I already had an unused cat5 from Betty's office to mine so I put the 5 port POE switch on one end and a new 5 port, Gb switch, in my office, on the other end. I put an 8 port, Gb, POE switch in my office and tied it to the 5 port Gb switch. I also connected the 5 port Gb switch to the new Cams Mini PC and the main switch. This allowed any host on the home net to access the CCTV net but the bulk of camera traffic stayed on the Video Net.