5. Create DMARC
From: https://www.linuxbabe.com/mail-server/create-dmarc-record
Part 5: Creating DMARC Record to Protect
Your Domain Name From Email Spoofing
In part 4 of building your own email server tutorial series (Ubuntu version,
CentOS/RHEL version), we implemented SPF and DKIM records to improve email
deliverability. In this part, we’re going to look at another email
authentication technology: DMARC. We will discuss how DMARC can benefit you,
how to create DMARC record and interpret DMARC report.
What is DMARC?
DMARC stands for Domain-based message authentication, reporting and
conformance. DMARC is not a product. It’s a freely available technical
specification and widely supported across the Internet. Anyone owning a
domain name can take advantage of DMARC.
A DMARC policy allows a domain owner to indicate that emails from his/her
domain is protected by SPF and DKIM. You can use DMARC to discover all
legitimate sources of email. DMARC builds upon two existing technologies:
SPF and DKIM.
DMARC Benefits
Why is DMARC good for you? The benefits of deploying DMARC are:
- Fraud detection: Phishers often spoof the From: header address to
impersonate big brands. DMARC is a powerful tool to fight against email
phishing and thus protect your brand.
- Simplified email delivery: Sending DMARC-compliant email allows receiving
email servers to simplify filtering rules.
- Your email domain reputation can be improved after you create DMARC record
correctly.
- Gives senders visibility into how receiving email servers process their
email. You can get a report of how many legitimate emails are sent from your
domain, how many emails can’t be authenticated including both legitimate
and fraudulent ones.
This is a pretty big deal to any organization that relies on email for its
day-to-day business. If you are doing email marketing, then DMARC is a must
-have tool to make email easy to deliver and reach customers. Pretty much
every major consumer-facing mailbox provider like Gmail, Yahoo and Microsoft
ask to be sent DMARC-compliant email to make their job of filtering emails
easier.
How to Create DMARC Record
DMARC policies are published as a TXT record in DNS.
Step 1: create SPF and DKIM records
Before creating a DMARC record, you must create SPF and DKIM records first.
Step 2: Identifier alignment
Send a test email from your domain, then check the raw email headers at the
recipient’s mailbox. You want to make sure the domains in Return Path,
From: header and d=domain in the DKIM signature are the same. If the 3
domains are identical, then they are aligned.
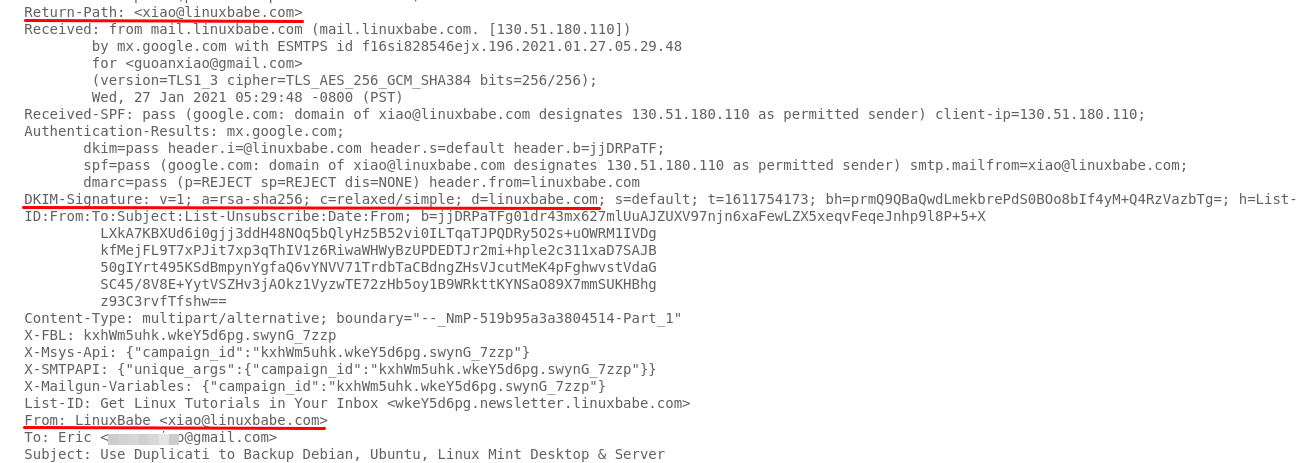 dmarc identifier alignment relaxed scalahosting VPS
If Return-Path or DKIM d= uses a subdomain instead of the main domain name,
then this is called relaxed alignment. If no subdomain is used and the main
domain names are the same, it’s called strict alignment.
Step 3: Setting up the DMARC record
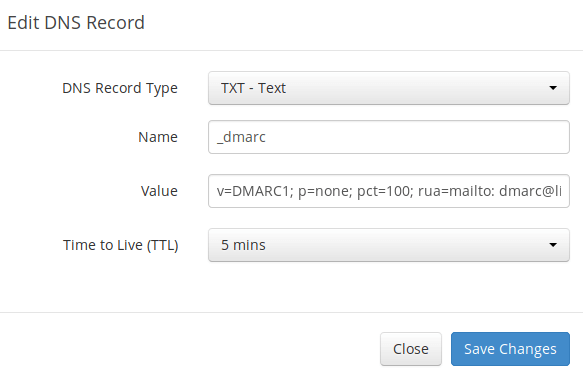
Go to your DNS manager and add a TXT record. In the name field, enter _dmarc.
In the value field, enter the following:
v=DMARC1; p=none; pct=100; rua=mailto:dmarc-reports@your-domain.com
dmarc identifier alignment relaxed scalahosting VPS
If Return-Path or DKIM d= uses a subdomain instead of the main domain name,
then this is called relaxed alignment. If no subdomain is used and the main
domain names are the same, it’s called strict alignment.
Step 3: Setting up the DMARC record
Go to your DNS manager and add a TXT record. In the name field, enter _dmarc.
In the value field, enter the following:
v=DMARC1; p=none; pct=100; rua=mailto:dmarc-reports@your-domain.com
 create dmarc record txt
create dmarc record txt
Explanation:
- v=DMARC1: The protocol version is DMARC1.
- p=none: We choose none as the policy for our domain.
- pct=100: The percentage of emails from your domain DMARC applies to
- rua stands for reporting URI for aggregate report. The email address is
used to tell receiving email servers where report should be sent. Replace
dmarc-reports@your-domain.com with your real email address that is used to
receive aggregate DMARC report.
There are 3 policies you can choose from:
- none: tells receiving email servers not to do anything special if DMARC
check fails.
- quarantine: tells receiving email server to put the email into quarantine
if DMARC check fails. It must be approved by an admin before it can reach
the recipient’s inbox.
- reject: tells receiving email servers to reject the email if DMARC check
fails. Note that not all receiving email servers comply with the reject
policy. Gmail and Yahoo Mail will reject the email, but Microsoft Mail
(Outlook, Hotmail, Live) doesn’t reject the email.
If your domain name has sent some emails before, thenp=none is a good start.
You should analyze the data for some time to see if there are legitimate
emails that don’t comply with DMARC. Once you have enough data and fix the
delivery problems, you can change the policy from none to quarantine or
reject.
If you have a new domain name that has never sent emails before, you can
skip none and quarantine and set p=reject.
There’s another tag that you can add to the DMARC record: fo. It has four
possible values.
- 0 (default): generate reports if all underlying authentication mechanisms
fail to produce a DMARC pass result
- 1: generate reports if any mechanisms fail.
- d: generate a report if DKIM signature failed verification.
- s: generate a report if SPF failed
I recommend using fo=1 first to generate more comprehensive DMARC failure
reports. When you change to a more restrictive policy, use fo=0.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:dmarck-reports@your-domain.com
You can check your DMARC record from Linux terminal with the following command:
dig txt +short _dmarc.example.com
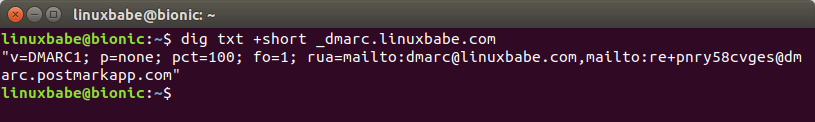 dmarc record check on linux
You can see that I used two email addresses to receive DMARC report, which I
will explain later. There’s another command-line tool (opendmarc-check)
that you can use to check DMARC record. It’s provided by the opendmarc
package.
sudo apt install opendmarc
opendmarc-check queries the DNS for a DMARC record for the named domain and
then translates the content found to a human-readable form.
dmarc record check on linux
You can see that I used two email addresses to receive DMARC report, which I
will explain later. There’s another command-line tool (opendmarc-check)
that you can use to check DMARC record. It’s provided by the opendmarc
package.
sudo apt install opendmarc
opendmarc-check queries the DNS for a DMARC record for the named domain and
then translates the content found to a human-readable form.
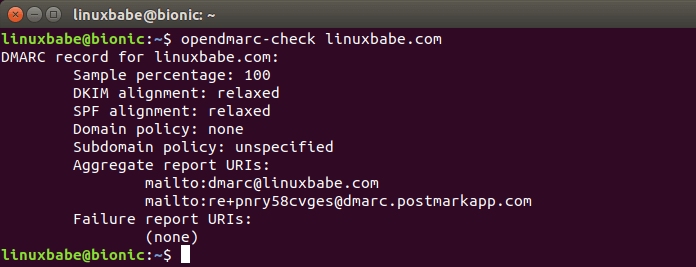 opendmarc-check
If you have a domain name that’s not going to send emails, you should use
p=reject policy.
v=DMARC1; p=reject; pct=100;
opendmarc-check
If you have a domain name that’s not going to send emails, you should use
p=reject policy.
v=DMARC1; p=reject; pct=100;
DMARC Test
A good service for DMARC test is https://www.mail-tester.com. Go to the
website, you will see a unique email address. Send an email from your domain
to this address and then check your score. (This website check all factors
that affect email deliverability, not just DMARC.) If DMARC passes, then you
will see something like below in the test result.
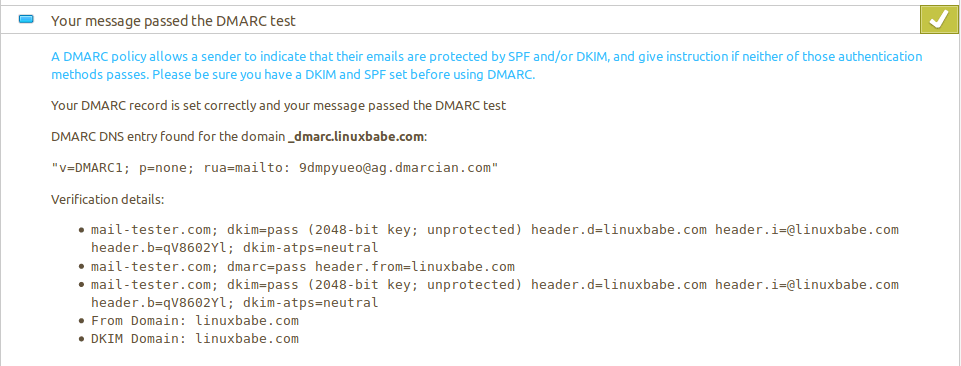 dmarc alignment test
Another way to test DMARC is send an email from your domain to your Gmail account.
If DMARC is configured correctly then you will see dmarc=pass in the
authentication-results header. (To view email headers in Gmail, click the Show Original
button, which can be found in the drop-down menu on the right side of
an opened email.)
dmarc alignment test
Another way to test DMARC is send an email from your domain to your Gmail account.
If DMARC is configured correctly then you will see dmarc=pass in the
authentication-results header. (To view email headers in Gmail, click the Show Original
button, which can be found in the drop-down menu on the right side of
an opened email.)
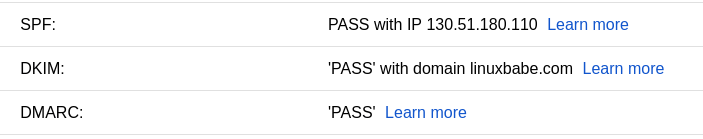 Gmail SPF and DKIM check scalahosting
To pass DMARC check, your emails need to meet one of the following
requirements.
Gmail SPF and DKIM check scalahosting
To pass DMARC check, your emails need to meet one of the following
requirements.
- SPF pass and the Return-Path: domain name is the same as the From: header
domain.
- DKIM pass and the d= domain in DKIM signature is the same as the From:
header domain.
By default, DMARC uses relaxed alignment. So the Return-Path domain or the
d= domain in DKIM signature can be a subdomain.
How to Interpret DMARC Report
There are two kinds of DMARC reports.
- Daily XML-based aggregate report generated by Gmail, Yahoo, Hotmail, etc.
- Real-time forensic reports (copies of individual pieces of email that fail
the DMARC check)
Normally you only want to receive the aggregate report. The data that DMARC
produces is invaluable for understanding what is going on for any given
email domain. However, raw DMARC report data is super hard to read and
understand. Luckily, Postmark offers a free service to process these
reports, presents you a much more readable report. The nice part about
Postmark is that you can tell receiving email servers to send XML reports
directly to Postmark for processing. So instead of entering your email
address in the DMARC record, you enter an email address of postmarkapp.com
that is unique to you.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.post
markapp.com;
You can also specify multiple email addresses, separated by commas.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.postmarkapp.com,mailto:dmarc-report@your-domain.com;
After your DMARC record has been verified by Postmark, you will receive a
DMARC report weekly every Monday in your email inbox. You don’t need to
register an account at Postmark.
Below is my first weekly report sent from Postmark. mcsignup.com belongs to
MailChimp, which is what I use to send newsletters to my mailing list. In my
SPF record, I actually allow MailChimp to send emails on my behalf, but I
didn’t know that they don’t use my domain name in the Return-Path header
for the signup confirmation emails. And they don’t sign emails using my
DKIM domain.
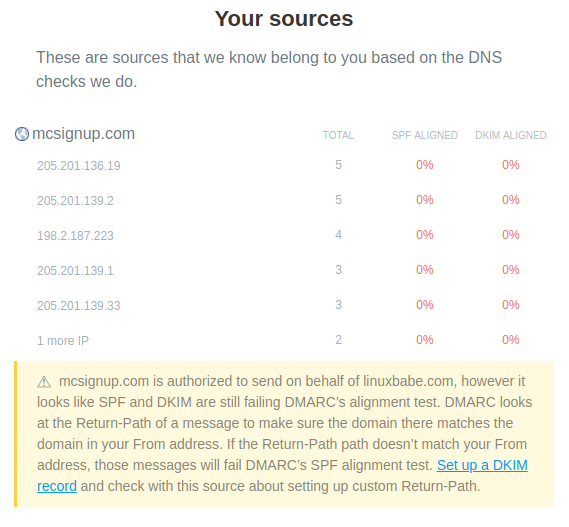 dmarc-report-analyzer-postmark
There’s also an unknown source that claims to be linuxbabe.com.
dmarc-report-analyzer-postmark
There’s also an unknown source that claims to be linuxbabe.com.
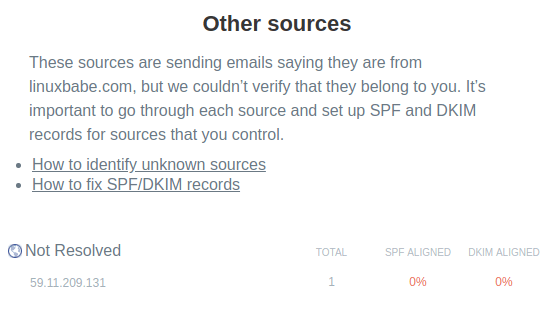 dmarc aggregate report
First, I always treat IP address that doesn’t have reverse DNS record as
spam. Then, to identify other unknown sources, I will check if it’s on an
email blacklist. debouncer.com tells me that it’s on 13 blacklists. So
clearly it’s a spammer trying to impersonate my domain name.
dmarc aggregate report
First, I always treat IP address that doesn’t have reverse DNS record as
spam. Then, to identify other unknown sources, I will check if it’s on an
email blacklist. debouncer.com tells me that it’s on 13 blacklists. So
clearly it’s a spammer trying to impersonate my domain name.
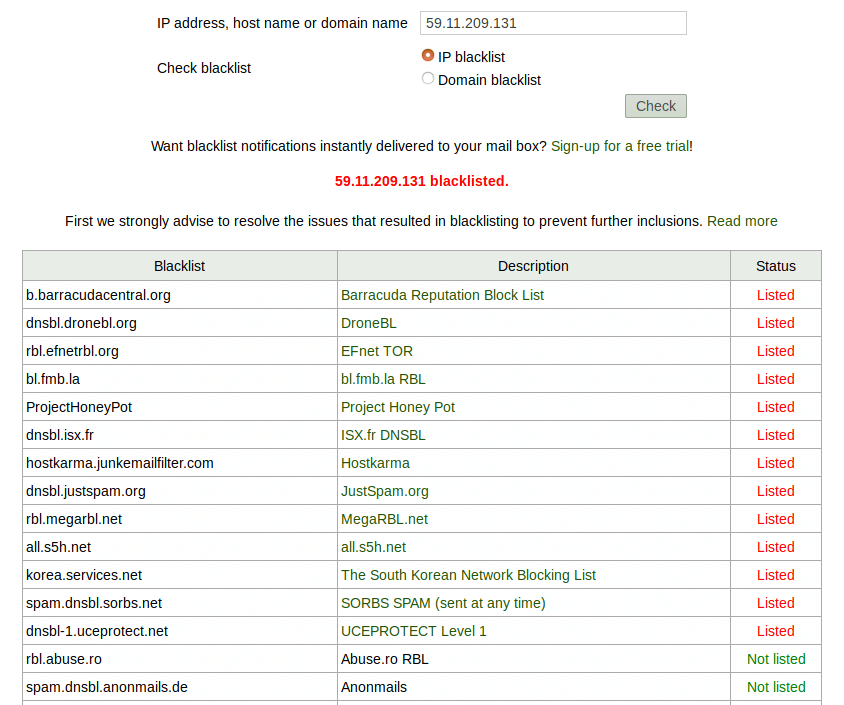 identify unkown sources in DMARC report
To better understand the unknown source and how your domains are used, you
can choose to receive forensic report by adding the ruf tag in DMARC record
like below.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.postmarkapp.com; ruf=mailto:forensic-report@your-domain.com;
The forensic report contains the copies of emails that failed DMARC check.
You can see the email headers, subject lines, and sometimes message body to
determine the nature of failed emails. If you recognize the subject line,
then it’s more likely to be a forwarded message. Note that some email
servers may choose to generate aggregate reports but not forensic report due
to privacy concerns and others may only include email headers in the
forensic report.
identify unkown sources in DMARC report
To better understand the unknown source and how your domains are used, you
can choose to receive forensic report by adding the ruf tag in DMARC record
like below.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.postmarkapp.com; ruf=mailto:forensic-report@your-domain.com;
The forensic report contains the copies of emails that failed DMARC check.
You can see the email headers, subject lines, and sometimes message body to
determine the nature of failed emails. If you recognize the subject line,
then it’s more likely to be a forwarded message. Note that some email
servers may choose to generate aggregate reports but not forensic report due
to privacy concerns and others may only include email headers in the
forensic report.
When does SPF or DKIM Fail?
A typical example of SPF failure is when your emails are relayed to the
destination email server through a third-party server. And the common
situation where DKIM fails is when your emails are sent through a mailing
list, which often adds additional headers or sentences to your emails.
Actually, a mailing list can cause SPF failure too.
There are two kinds of mailing lists.
- Announcement mailing list. Typically used by websites to send newsletters.
The mailing list owner can send messages to a large number of subscribers,
whereas subscribers can only reply to the mailing list owner.
- Discussion mailing list, where subscribers can send messages to all other
subscribers. This is common in the open-source community. GNU mailman is the
most popular software to set up such a mailing list.
This first kind is easy to tackle because the domain owner is a customer of
the mailing list server provider. It’s easy to add the mailing list server
to SPF record. Also, the mailing listing server can do DKIM signing for
customers.
The second kind of mailing list is difficult to tackle for domain owners who
have users participating in discussions in various mailing lists. The domain
owner can’t list all possible discussion mailing list servers in SPF
record, and these mailing lists can’t do DKIM signing for other domain
names. A possible solution is that the mailing list uses its own address in
the From: header, and adds the original email sender’s address in the
Reply-To: header. More details can be found on this GNU mailman wiki page. A
more practical and promising solution is ARC (Authentication Received
Chain), which basically means that mailing lists do DMARC check and sign the
DMARC result. Receiving email servers can trust the ARC signature and
override local DMARC check results.
When Should You Switch to p=reject Policy
You should wait enough time to receive lots of DMARC report. Don’t be
surprised when you see false positives in your DMARC report. Analyze these
false positives and take action to make sure they can pass DMARC check.
After that, switch your DMARC policy to p=quarantine and eventually
p=reject. Do not skip quarantine and go straight to reject. When you switch
to a more strict DMARC policy, consider changing the value of pct tag.
So the overall process goes like this:
- p=none; pct=100;
- p=quarantine; pct=30;
- p=quarantine; pct=70;
- p=quarantine; pct=100;
- p=reject; pct=30;
- p=reject; pct=70;
- p=reject; pct=100;
Why I’m still using p=none policy?
Firstly, it’s because of Microsoft. mails forwarded from Microsoft Outlook
Mailbox can fail DKIM check, which is bad. For this reason, I cannot set my
DMARC policy to quarantine or reject.
Another reason is that I’m using MailChimp to send newsletters to my email
subscribers. MailChimp uses its own domain in the Return-Path header and its
own DKIM signature for the signup confirmation email, which causes DMARC
failure.
The solution to the first problem is deploying ARC (Authenticated Received
Chain). Until ARC is implemented on Mailbox providers, I won’t change my
DMARC policy.
To solve the second problem, I need to switch to a self-hosted newsletter
app like Mailtrain, instead of using an email service provider (ESP) to send
newsletters to email subscribers. That way, I can use my own domain name in
the Return-Path header and my own DKIM signature in every email. However,
this also means I will need to build a good reputation for my email domain
and the IP address of my email server so that my emails can land in my
subscribers’ inbox instead of the spam folder. That can take some time and
effort.
Update (April 19, 2019)
DKIM alignment in emails forwarded by Microsoft Outlook has improved. Also
in February 2019, Mailchimp started using the customer’s domain name in
the DKIM signature for the signup confirmation emails, so all Mailchimp
emails are now DKIM-aligned. I now begin experimenting with the p=quarantine
policy and eventually will switch to the p=reject
policy.
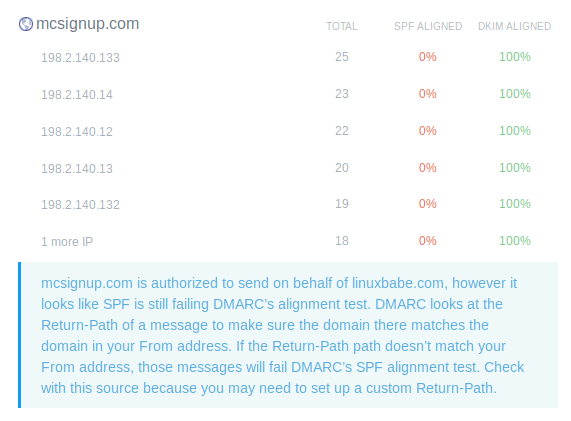 mcsignup dkim alignment
mcsignup dkim alignment
Wrapping Up
Having a p=none policy is better than having no DMARC record. Although
p=none cannot prevent email spoofing, at least my legitimate emails have a
better chance to be placed in inbox.
I hope this article helped you understand and deploy DMARC policy. In part
6, I will share with you all my tips on how to get your emails into the
recipient’s inbox instead of the spam folder.
How to Stop Your Emails Being Marked as Spam
As always, if you found this post useful, subscribe to our free newsletter
or follow us on Twitter or like our Facebook page.
 dmarc identifier alignment relaxed scalahosting VPS
If Return-Path or DKIM d= uses a subdomain instead of the main domain name,
then this is called relaxed alignment. If no subdomain is used and the main
domain names are the same, it’s called strict alignment.
Step 3: Setting up the DMARC record
Go to your DNS manager and add a TXT record. In the name field, enter _dmarc.
In the value field, enter the following:
v=DMARC1; p=none; pct=100; rua=mailto:dmarc-reports@your-domain.com
dmarc identifier alignment relaxed scalahosting VPS
If Return-Path or DKIM d= uses a subdomain instead of the main domain name,
then this is called relaxed alignment. If no subdomain is used and the main
domain names are the same, it’s called strict alignment.
Step 3: Setting up the DMARC record
Go to your DNS manager and add a TXT record. In the name field, enter _dmarc.
In the value field, enter the following:
v=DMARC1; p=none; pct=100; rua=mailto:dmarc-reports@your-domain.com
 create dmarc record txt
create dmarc record txt
 dmarc record check on linux
You can see that I used two email addresses to receive DMARC report, which I
will explain later. There’s another command-line tool (opendmarc-check)
that you can use to check DMARC record. It’s provided by the opendmarc
package.
sudo apt install opendmarc
opendmarc-check queries the DNS for a DMARC record for the named domain and
then translates the content found to a human-readable form.
dmarc record check on linux
You can see that I used two email addresses to receive DMARC report, which I
will explain later. There’s another command-line tool (opendmarc-check)
that you can use to check DMARC record. It’s provided by the opendmarc
package.
sudo apt install opendmarc
opendmarc-check queries the DNS for a DMARC record for the named domain and
then translates the content found to a human-readable form.
 opendmarc-check
If you have a domain name that’s not going to send emails, you should use
p=reject policy.
v=DMARC1; p=reject; pct=100;
opendmarc-check
If you have a domain name that’s not going to send emails, you should use
p=reject policy.
v=DMARC1; p=reject; pct=100;
 dmarc alignment test
Another way to test DMARC is send an email from your domain to your Gmail account.
If DMARC is configured correctly then you will see dmarc=pass in the
authentication-results header. (To view email headers in Gmail, click the Show Original
button, which can be found in the drop-down menu on the right side of
an opened email.)
dmarc alignment test
Another way to test DMARC is send an email from your domain to your Gmail account.
If DMARC is configured correctly then you will see dmarc=pass in the
authentication-results header. (To view email headers in Gmail, click the Show Original
button, which can be found in the drop-down menu on the right side of
an opened email.)
 Gmail SPF and DKIM check scalahosting
To pass DMARC check, your emails need to meet one of the following
requirements.
Gmail SPF and DKIM check scalahosting
To pass DMARC check, your emails need to meet one of the following
requirements.
 dmarc-report-analyzer-postmark
There’s also an unknown source that claims to be linuxbabe.com.
dmarc-report-analyzer-postmark
There’s also an unknown source that claims to be linuxbabe.com.
 dmarc aggregate report
First, I always treat IP address that doesn’t have reverse DNS record as
spam. Then, to identify other unknown sources, I will check if it’s on an
email blacklist. debouncer.com tells me that it’s on 13 blacklists. So
clearly it’s a spammer trying to impersonate my domain name.
dmarc aggregate report
First, I always treat IP address that doesn’t have reverse DNS record as
spam. Then, to identify other unknown sources, I will check if it’s on an
email blacklist. debouncer.com tells me that it’s on 13 blacklists. So
clearly it’s a spammer trying to impersonate my domain name.
 identify unkown sources in DMARC report
To better understand the unknown source and how your domains are used, you
can choose to receive forensic report by adding the ruf tag in DMARC record
like below.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.postmarkapp.com; ruf=mailto:forensic-report@your-domain.com;
The forensic report contains the copies of emails that failed DMARC check.
You can see the email headers, subject lines, and sometimes message body to
determine the nature of failed emails. If you recognize the subject line,
then it’s more likely to be a forwarded message. Note that some email
servers may choose to generate aggregate reports but not forensic report due
to privacy concerns and others may only include email headers in the
forensic report.
identify unkown sources in DMARC report
To better understand the unknown source and how your domains are used, you
can choose to receive forensic report by adding the ruf tag in DMARC record
like below.
v=DMARC1; p=none; pct=100; fo=1; rua=mailto:unique-to
-you@dmarc.postmarkapp.com; ruf=mailto:forensic-report@your-domain.com;
The forensic report contains the copies of emails that failed DMARC check.
You can see the email headers, subject lines, and sometimes message body to
determine the nature of failed emails. If you recognize the subject line,
then it’s more likely to be a forwarded message. Note that some email
servers may choose to generate aggregate reports but not forensic report due
to privacy concerns and others may only include email headers in the
forensic report.
 mcsignup dkim alignment
mcsignup dkim alignment