Firewall builder
Firewall Builder
I built this little tool back in the late-1900s when I started hosting
ary.com, it has served me well over the years.
Configuring firewalls is a critical operation since one mistake can allow
public access to vulnerable systems. Command line firewall configuration is
mistake prone due to the tedious nature of firewalls and the lack of
understanding of network traffic and how firewalls work. A single blocking may
require several actual rules. The firewall's flexibility acts to be it's own
worst enemy since it complicates configuration, increasing the incidence of
errors.
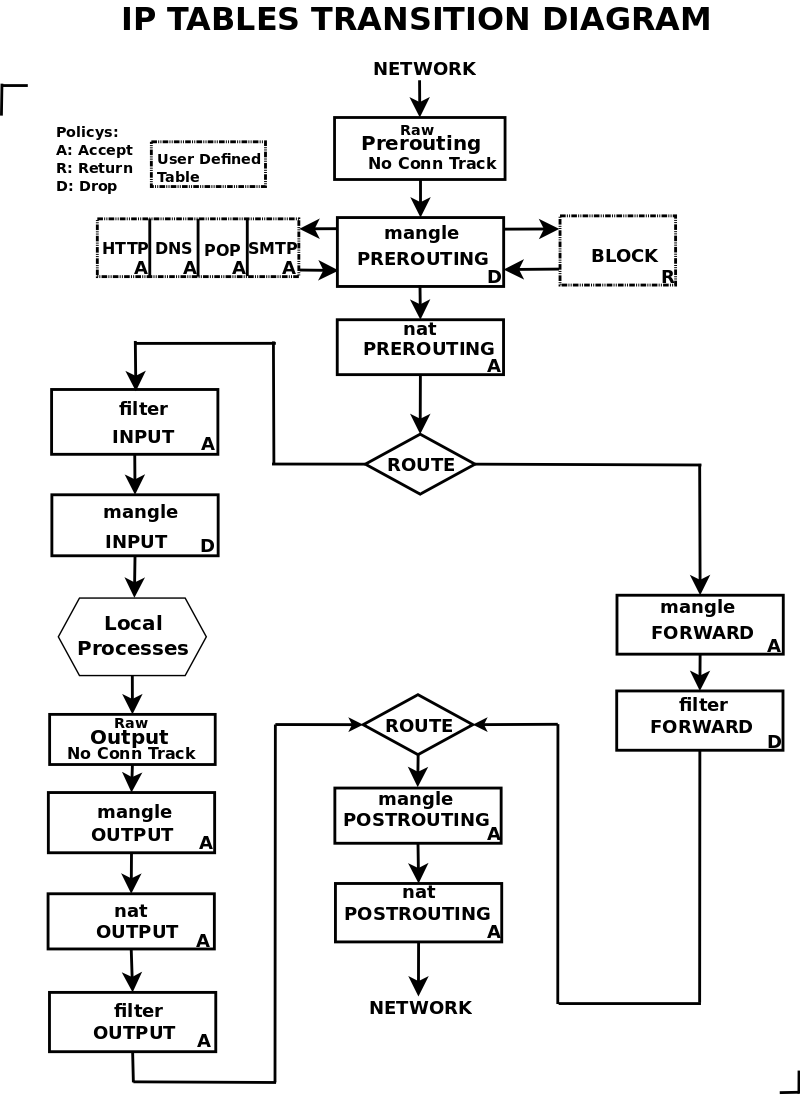
When building a firewall tool you must be familiar with the IPTABLES Transition table.
Firewall builder is addressed to this premise.
Firewall builder is a simple way to build an iptables firewall without needing
to understand the ins and outs of iptables. To this end, we have defined a
"firewall builder language" to describe what we want done.
It is assumed that Firewall builder will stop any packet that we don't
specifically allow.
We are only interested in IP and it's sub-protocols since others are blocked by
the firewall.
Firewall builder language contains a number of keywords each followed by a
consistent set of arguments.
All but the NIC and CIDR keywords (defines) have the same argument list in
the same order.
Arguments are frequently omitted but they are always in the same order.
In general, the more arguments present, the more we restrict the group of
packets the rule affects.
A crunch '#' (poundsign) denotes a comment contained in the remainder of the
line, hence may follow a keyword argument set.
The firewall definition is in a file with the extension of '.def' and contains
the rules governing packet flow through the firewall.
Argument List:
[ifc] [proto] [cidr] [:port] [TO [ifc] [cidr] [:port]]
The arguments are broken int two sets of 4.
The elements of each set are:
- 'ifc' the interface, either ethN or a previously defined name like EXT1, for
an external network interface.
- 'proto' the protocol, like tcp, udp, icmp, or a numeric ip protocol number.
Also note that 'proto' is omitted from the destination set since the
packet's protcol isn't changed.
- 'cidr' Classless Internet Domain Routing, the network ip and netmask for
packets of interest to the current rule.
- ':port' the tcp or udp port number.
The 1st set are normally source description set followed by 'TO' and the
destination set. Please note the destination set is identical to the source
set with 'proto' (protocol) omitted.
Key Words:
NIC: define a network interface by a pseudo name, like NIC EXT eth1
CIDR: define a network/mask by a pseudo name, like CIDR MEPUb
68.88.218.240/29
ACCEPT: Accept a packet into the firewall processes themselves like ssh.
ALLOW: Allow packets to flow from the source CIDR to the TO CIDR.
ALLOW 192.168.0.0/16 TO 171.16.0.0/16
Allow the internal net to access the DMZ.
BLOCK: block packets from a specific network to an optional distination network
REDIRECT: redirect specific packets originally destined to the first address to
a new IP and port.
SNAT: source nat outbound packets to our public network IPs so they will return
to us.
A simple firewall example
# ALL ARGUMENTS: [ifc] [proto] [cidr] [:port] [TO [ifc] [cidr] [:port]]
NIC DMZ eth2
NIC EXT eth1
CIDR MELOC localhost
CIDR MEPUb 68.88.218.240/29
CIDR NETPUb 68.88.218.240/29
CIDR NETLOC 192.168.0.0/16
CIDR WWW3 68.88.218.243
CIDR WWW3LOC 192.168.0.108
CIDR NS2PUb 68.88.218.242
CIDR NS2LOC 192.168.0.108
BLOCK EXT 66.180.160.0/20 TO :53
BLOCK EXT tcp 71.64.0.0/12 TO :25
BLOCK EXT tcp 71.64.0.0/12 TO :80
BLOCK EXT tcp 71.80.0.0/12 TO :25
BLOCK EXT tcp 72.224.0.0/13 TO :25
BLOCK EXT tcp 150.0.0.0/8 TO :80
BLOCK EXT tcp 155.0.0.0/8 TO :80
BLOCK EXT 202.0.0.0/8 TO :53
BLOCK EXT 203.0.0.0/8 TO :53
BLOCK EXT tcp 209.85.0.0/8 :80
BLOCK EXT tcp 209.237.0.0/8 :80
REDIRECT EXT udp NS2PUb :53 TO NS2LOC
REDIRECT EXT tcp :25 TO 192.168.0.108
ACCEPT eth0 tcp NETLOC TO :22
ACCEPT eth0 tcp 192.168.0.2 TO :80
ACCEPT eth0 tcp 192.168.0.2 TO :25
ALLOW 77.66.55.44/31 TO 192.168.0.108 :22
SNAT eth0 NS2LOC :53 TO eth1 NS2PUb # Src NAT Local Net to the Public net
SNAT eth0 NETLOC TO eth1 NETPUb
# SNAT eth0 TO eth1 68.88.218.243 # TEST USAGE MSG
IPTABLES TRANSITION DIAGRAM